If you’ve ever wanted to know more about Android penetration testing, this blog post is for you. Android has become the most popular smartphone operating system in the world. Consequently, Android penetration testing is quickly becoming one of the hottest topics in information security. This article will discuss what Android penetration testing entails and the steps you need to follow to perform it. We’ll also go over some tools to help make your life easier when doing an Android pentest!
What is Android Penetration Testing?
Android penetration testing is also known as Android pen-testing or Android app security auditing. It is the practice of testing a mobile application to scan vulnerabilities that hackers could exploit. These vulnerabilities can result in:
- leaks of sensitive data stored on the device (such as usernames and passwords)
- access to private information displayed on the screen (such as bank account details)
- unauthorized control over other applications installed on your device
- sending premium-rate SMS messages from your phone without you knowing about it
- eavesdropping on calls made using voice over IP apps like Skype or Viber.
Stages of Android Penetration Testing
You can roughly divide an android penetration test into five stages. Let’s look at each step individually:
1. Reconnaissance
Android penetration testing begins with surveillance, where you gather as much information as possible about your target application.
2. Threat Modeling and & Vulnerability Identification:
Android penetration testing also involves identifying and prioritizing the most critical vulnerabilities in your Android application. This is done by performing a threat model on your Android app, which identifies any potential weaknesses or flaws that can be used to exploit it.
Android apps often have an accompanying web service to store data and communicate between devices or even across multiple applications on the same device itself. These endpoints are usually not correctly secure, making it a prime location for attackers to exploit.
3. Exploitation
Android penetration testing, like Android app security, generally focuses on identifying and prioritizing potential vulnerabilities in Android apps. Once the most critical ones have been identified, you can exploit them to see if they are indeed exploitable or not.
4. Post-Exploitation
Android pen-testing involves checking if the vulnerabilities you’ve exploited are exploitable and then steps to patch them.
Tools Used: Burp Suite Pro, Astra Security Suite, DroidBox (JEB), CuckooDroid, and several others, which can be found here. The tools mentioned in this Android pentesting blog post are just a few examples of what you can use.
5. Resolution & Retesting
Android penetration testing Android apps is not complete if you do all of this and forget about it. Android pentesting is done periodically to ensure that the vulnerabilities found earlier on continue to exist or have been patched.
After patching everything up, you also need to retest to ensure the changes you made are effective.
Steps & Tools for Android Penetration Testing
These are two steps that you have to include in your android penetration test:
1. Network Proxy
Android apps communicate over the network using Android Interface Definition Language (AIDL), Android IPC, or Android RPC. These can be intercepted by a proxy to determine what data is being sent and received within your application
2. Analyzing the Source Code
Before you start performing an Android penetration test, you must look at your source code and identify any security issues with it. Otherwise, your Android pentest may not have much success.
Android apps contain AndroidManifest.xml files. They are helpful to determine what permissions an app requires for it to run and whether these are needed for the function of that application or not (i.e., you might find that your banking app requests permission called android permission). Android apps also contain res/XML folders that hold all XML files (such as AndroidManifest.xml).
Tools You Can Use:
QARK (Quick Android Review Kit): QARK is a tool that you can use to automate Android penetration testing. You can use QARK for all the five stages of Android pentesting mentioned in this article.
APKTool: APKTool is an Android app that you can use for decompiling, analyzing, and modifying Android APK files. You can explore decompiled Android apps to find hardcoded Android app secrets such as hardcoded Android API keys and tokens, Android app signing certificates, etc.
DroidBox: Droidbox is a tool that uses machine learning to analyze Android applications. Droidbox can identify common security vulnerabilities in Android apps, both at the source code level and bytecode level, without requiring Android source code.
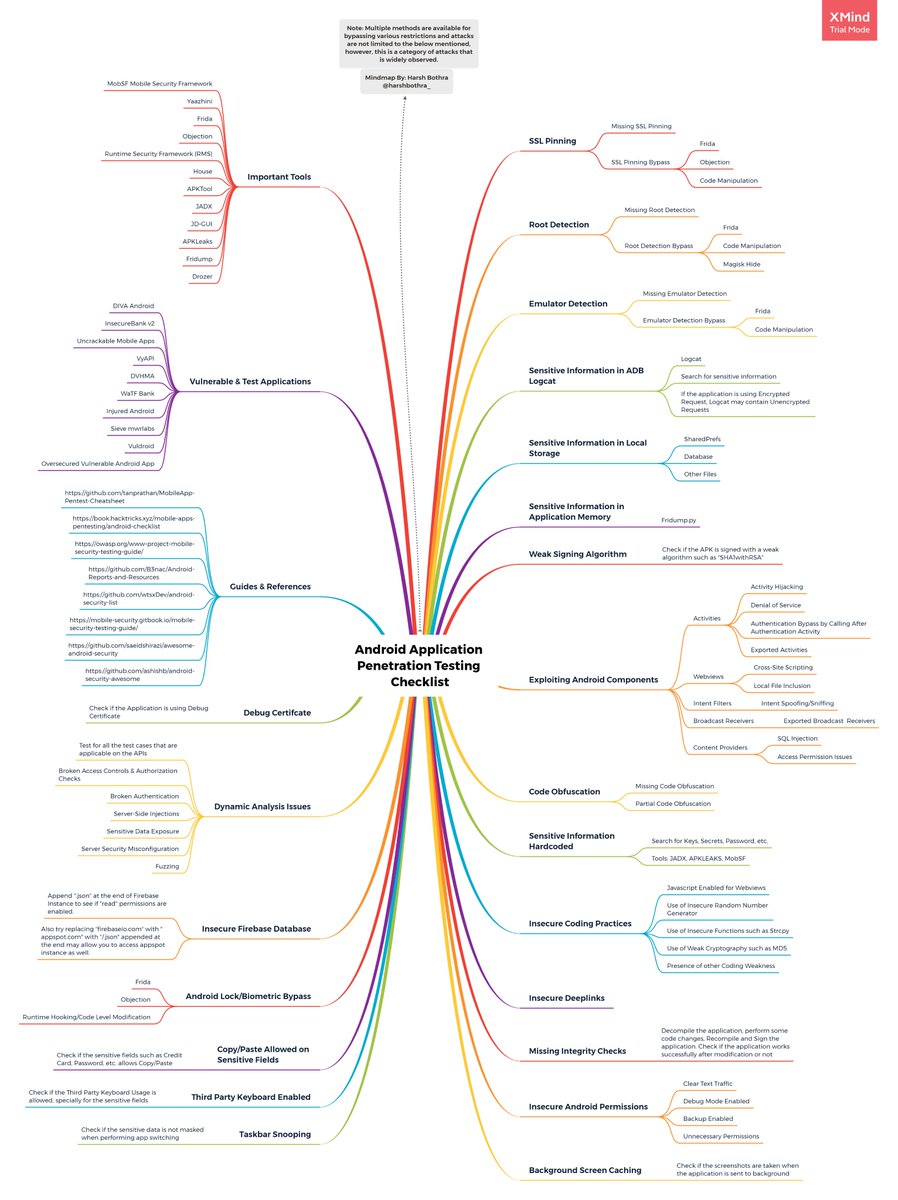
Source: XMind
Conclusion
Android penetration testing is a method of securing your app from threats. This article covers the basics of knowledge about this type of security, including how to perform it and steps for getting started. So, follow these steps and instructions on how to perform the assessment correctly. We hope that all of your projects go smoothly!













Comments